About
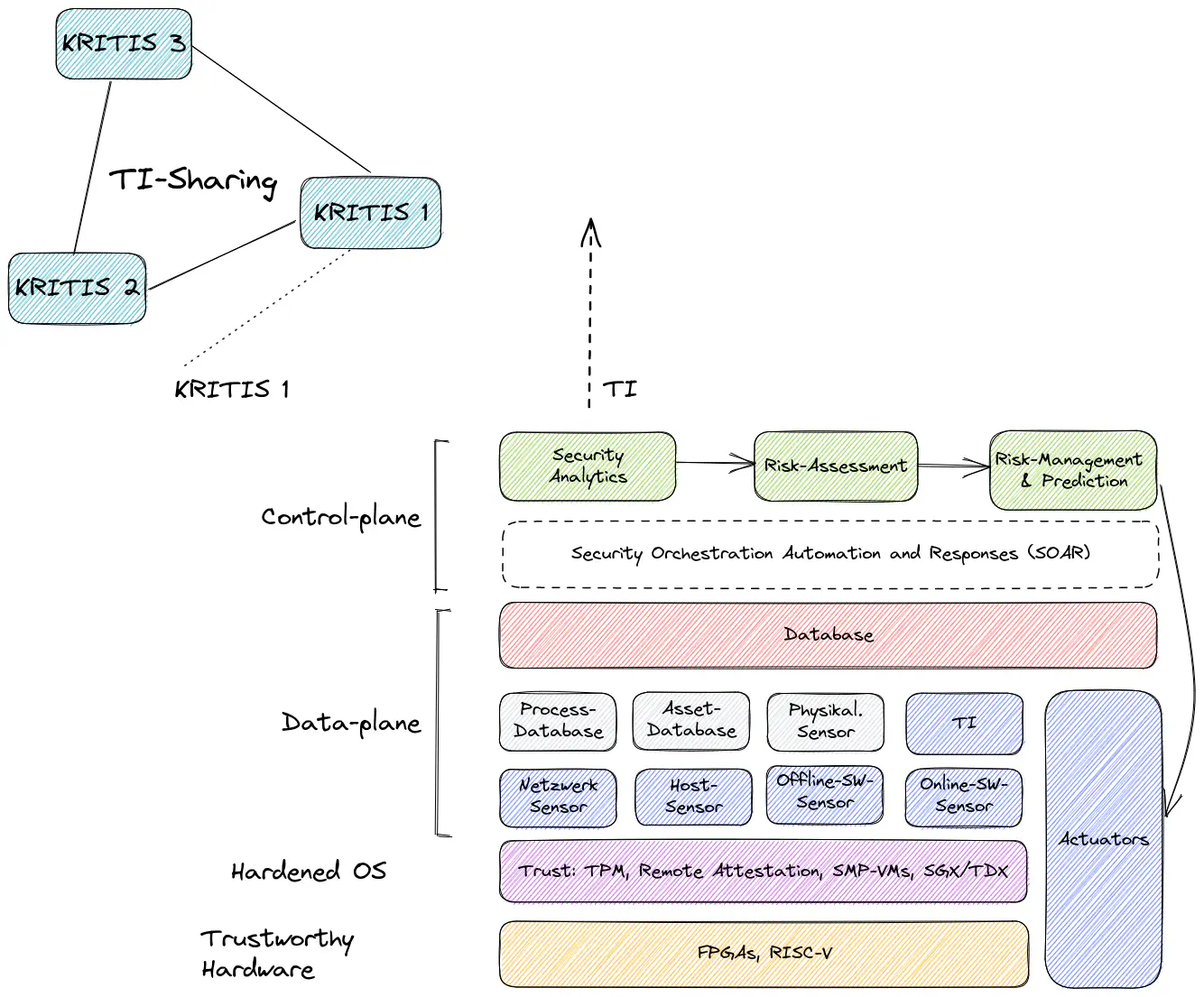
SOVEREIGN takes a holistic approach to enhance the cyber security of critical infrastructures and will develop a resilient, AI- and zero-trust-based cyber defense platform (see Figure 1). Designed as modular building blocks, the platform brings passive and active sensors and actuators deep into critical infrastructures to detect, assess, treat, and defend against security breaches as well as complex cyber attacks at an early stage. A decentralized data plane makes data available and persists it on demand.
The platform will use AI to automatically predict, detect, and evaluate attacks and, based on this, dynamically assess the risk to business processes and assets. It will also suggest appropriate countermeasures, their sequence and precise timing. These measures are executed either after feedback from a security expert or - after a learning phase - possibly completely autonomously. This prevents “alarm fatigue” among deployed personnel and enables efficient staff deployment. The platform will also be able to share and operationalize threat intelligence in the form of Tactics, Techniques and Procedures (TTP) as well as complete cases (concrete attack scenarios) with other critical infrastructures (and their SOVEREIGN instances) in a privacy-protecting manner while maintaining company and business secrets. In this way, not only individual critical infrastructures and networks, but entire sectors can be protected more efficiently.
Even if critical infrastructures cannot be completely technologically sovereign, e.g., because certain manufacturers are indispensable, the SOVEREIGN platform embedded in them will be technologically sovereign. To this end, the platform will be based entirely on existing open-source software and open hardware (e.g., RISC-V) and will also be developed as open-source itself. Parts of the platform functionality will also be developed directly in hard-to-attack but reconfigurable hardware (FPGAs). Furthermore, the platform will bring self-healing and reconfiguration capabilities. In addition to reconfiguring “softwareized” networks and the systems connected to them, the platform will above all be able to reconfigure itself. A detected, successful attack on a component of the platform should not be possible a second time. To this end, the platform will independently patch the detected, exploited software vulnerabilities or vulnerabilities in the reconfigurable hardware.
